by R.I. Pienaar | Mar 21, 2009 | Usefull Things
A lifetime ago when I still gave a damn for FreeBSD I wrote about ipfw tables, I still really love ipfw’s simple syntax and really wish there was something similar for Linux rather than Human Error Guaranteed convoluted syntax mess that’s iptables.
Anyway, so in my case I have machines all over, one off VPS machines, dom0’s with a subnet routed to them and so forth. I often have rules that need to match on all my ips, things like allow data into my backup server, allow config retrieval from my puppetmaster etc. I do not want to maintain my total list of ips 10 times over so how to deal with it?
This is a good fit for ipfw tables, you create a table – essentially an object group like in a Cisco PIX or ASA – and then use it to match source IPs.
In the last week I’ve asked quite a few people how they’d do something similar with iptables but no-one seemed to know, I had people who were happy to maintain the same list many times. People who would use tools like sed to insert it into their rules and everything in between. I think I know a better way so I figured I’ll blog about it because it’s obviously something people do not just understand.
Iptables ofcourse use chains, and you can jump to and from chains all you want, this is very simple, so lets create a chain with all my IPs
-A my_ips -s 192.168.1.1 -m comment –comment “box1.com” -j ACCEPT
-A my_ips -s 192.168.2.1 -m comment –comment “box2.com” -j ACCEPT
-A my_ips -s 192.168.3.1 -m comment –comment “box3.com” -j ACCEPT
This creates a chain my_ips that just accepts all traffic from my IP addresses, now lets see how we’d allow all my ip addresses into my webserver?
-A INPUT -p tcp –dport 80 -m tcp -j my_ips
So this is something almost as good as a ipfw table, I can reuse it many times on many machines and my overall configuration is much more simple. It’s not quite as powerful as a table but for my needs it’s fine.
Combined with a tool like Puppet that manages your configurations you can ensure that this chain is installed on any machine that uses iptables, ready to be used and also trivial to update whenever you need too without having to worry about human error incurred from having to maintain many copies of essentially the same data.
In my environment when I update this table, I check it into SVN and within 30 minutes every machine in my control has the new table and they’ve all reloaded their iptables rules to activate it. Testing is very easy since puppet allows you to use environments similar to Rails has and so if I really need to I can easily test firewall changes on a small contained set of machines, distributed object group management with version control and everything rolled into one.
by R.I. Pienaar | Mar 19, 2009 | Uncategorized
I had a thought recently when dealing with Apple and Microsoft on warranty fixes just how different things are, thought I’d sum up my experiences here:
Dell
I had a 15 inch Dell laptop, 3 year extended on-site warranty that I purchased to cover any issues. During the time I had the laptop it all worked well except the battery died after about 2 years.
Contacted Dell about this, they pointed out batteries are consumables and so not covered, that was expected. The kicker though was that I couldn’t even buy a new battery from them because since they only covered batteries for the 1st year, and the machines has been off the production lines for more than a year they simply stopped making them.
2 year old laptop, 1 year left on it’s warranty and it was useless, awesome.
Microsoft
My Xbox 360 is showing the dreaded 3 red lights of death, Microsoft has admitted the problem and offers a 3 year extended warranty for this problem. I went to their site, saw I can book the machine in online for fixing, after filling everything in the page said it’s not available in my country, contact support.
Contact support, tell them the problem and clearly point out I have filled in the form and that I am in the UK and thus not covered by the service offered by the form. Support droid points me back to the same support page, but warning me that its not covered in all countries and that I should contact them if I am not covered.
I’ve gone through this little circle jerk 4 times now, each time with the same circular logic applied by the drones, I’m about to just towel fix the 360 or upgrade to a 360 Elite.
Apple
I have a black 1.5 year old macbook, it’s pretty sweet but so far I’ve had a HDD and a battery die on me. It too is on 3 year extended warranty.
The HDD dying was inconvenient, I had to book in with a Genius but they swapped it witout question or cost, I just had to reinstall my stuff – easily done with time machine. I walk past an Apple Temple daily so no biggie there, they kept to their time schedules and the booking went smooth as can be, 3 days later my macbook was fixed.
When the battery died they first said its a consumable and not covered, I pointed out it died suddenly and not gradually and so it must be a fault rather than consumption. They posted free of charge a new battery, and paid for the old one to go back. The next battery arrived the next day without fault.
So all things considered, so far the Apple tax has proven a absolute bargain to me.
by R.I. Pienaar | Mar 17, 2009 | Code
I’ve been playing a bit with Stomp and ActiveMQ to help with some of my distributed management problems so needed a nice generic client for it.
I wrote one in Ruby, the code can be found here, you’ll need the Stomp rubygem to use it.
To use it set environment variables STOMP_USER and STOMP_PASSWORD and run it as below, you can also pass the user/pass to it as command line options but that will expose your password in ps output.
% stompclient --server your.server
AMQ> subscribe /topic/foo
Subscribing to /topic/foo
AMQ> /topic/foo bar
Sending 'bar' to /topic/foo
13:48:49:/topic/foo> bar
AMQ> detail
No longer showing details
AMQ> /topic/foo bar
Sending 'bar' to /topic/foo
bar |
% stompclient --server your.server
AMQ> subscribe /topic/foo
Subscribing to /topic/foo
AMQ> /topic/foo bar
Sending 'bar' to /topic/foo
13:48:49:/topic/foo> bar
AMQ> detail
No longer showing details
AMQ> /topic/foo bar
Sending 'bar' to /topic/foo
bar
So it’s just a simple little frontend, it uses Ruby’s readline library which slows things down a bit as it does some blocking polling of input, if you’re sending loads of messages directed at this client it will seem a bit sluggish, unavoidable unfortunately.
by R.I. Pienaar | Mar 11, 2009 | Usefull Things
In the 7 or 8 years I’ve been living in the UK I’ve never been near a fast ADSL exchange, this has all now changed since moving last week and now I can get a BE link, it really is amazing to go from a shoddy 2 Mbit link to 17ish one, see below.
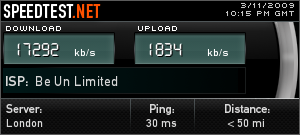
I only activated it this morning, so yet to see if it will be more stable than my previous link which used to drop 3 to 5 times daily, but hopefully now I’ll be abe to play Xbox games while my partner browse stuff, something which previously was totally out of the question.
by R.I. Pienaar | Jan 26, 2009 | Front Page, Usefull Things
I’ve previously mentioned the really great syscfg integrated IPSEC on RedHat Linux here but thought I’d now show a real world example of a Cisco ASA and a RedHat machine talking since it is not totally obvious and it is not something I seen specifically documented anywhere using Google.
A quick recap: RedHat now lets you build IPSEC VPNs using just simple ifcfg-eth0 style config files.
I’ll quickly show both sides of the config to build a site to site VPN, Site A is a Linux machine with a real IP address while Site B is a Cisco ASA with a private network behind it, the Linux machine has this in /etc/sysconfig/network-scripts/ifcfg-ipsec1:
TYPE=IPSEC
ONBOOT=yes
IKE_METHOD=PSK
SRCGW=1.2.3.4
DSTGW=2.3.4.5
SRCNET=1.2.3.4/32
DSTNET=10.1.1.0/24
DST=2.3.4.5
AH_PROTO=none |
TYPE=IPSEC
ONBOOT=yes
IKE_METHOD=PSK
SRCGW=1.2.3.4
DSTGW=2.3.4.5
SRCNET=1.2.3.4/32
DSTNET=10.1.1.0/24
DST=2.3.4.5
AH_PROTO=none
The pre-shared key is in /etc/sysconfig/network-scripts/keys-ipsec1 as per the RedHat documentation.
The Cisco ASA does not support AH so the big deal here is to disable AH which turns out to be the magic knob to tweak here to make it work.
In this case the Linux Server on Site A has the IP address 1.2.3.4 while the ASA is running on 2.3.4.5, the private network at Site B is 10.1.1.0/24.
On the Cisco the relevant lines of config are:
object-group network siteb_to_sitea_local_hosts
description Site B to Site A VPN Local hosts
network-object 10.1.1.0 255.255.255.0
object-group network siteb_to_sitea_remote_hosts
description Site B to Site A VPN Remote Hosts
network-object 1.2.3.4 255.255.255.255
access-list siteb_to_sitea_vpn extended permit ip object-group siteb_to_sitea_local_hosts object-group siteb_to_sitea_remote_hosts
access-list inside_nat_bypass extended permit ip object-group siteb_to_sitea_local_hosts object-group siteb_to_sitea_remote_hosts
nat (inside) 0 access-list inside_nat_bypass
crypto map outside_map 20 match address siteb_to_sitea_vpn
crypto map outside_map 20 set pfs
crypto map outside_map 20 set peer 1.2.3.4
crypto map outside_map 20 set transform-set ESP-3DES-SHA
crypto map outside_map 20 set security-association lifetime seconds 3600
crypto map outside_map 20 set security-association lifetime kilobytes 4608000
crypto map outside_map interface outside
crypto isakmp enable outside
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto isakmp policy 20
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 28800
tunnel-group 1.2.3.4 type ipsec-l2l
tunnel-group 1.2.3.4 ipsec-attributes
pre-shared-key secret |
object-group network siteb_to_sitea_local_hosts
description Site B to Site A VPN Local hosts
network-object 10.1.1.0 255.255.255.0
object-group network siteb_to_sitea_remote_hosts
description Site B to Site A VPN Remote Hosts
network-object 1.2.3.4 255.255.255.255
access-list siteb_to_sitea_vpn extended permit ip object-group siteb_to_sitea_local_hosts object-group siteb_to_sitea_remote_hosts
access-list inside_nat_bypass extended permit ip object-group siteb_to_sitea_local_hosts object-group siteb_to_sitea_remote_hosts
nat (inside) 0 access-list inside_nat_bypass
crypto map outside_map 20 match address siteb_to_sitea_vpn
crypto map outside_map 20 set pfs
crypto map outside_map 20 set peer 1.2.3.4
crypto map outside_map 20 set transform-set ESP-3DES-SHA
crypto map outside_map 20 set security-association lifetime seconds 3600
crypto map outside_map 20 set security-association lifetime kilobytes 4608000
crypto map outside_map interface outside
crypto isakmp enable outside
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto isakmp policy 20
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 28800
tunnel-group 1.2.3.4 type ipsec-l2l
tunnel-group 1.2.3.4 ipsec-attributes
pre-shared-key secret
Using these specific phase 1 and phase 2 parameters – timings, pfs, crypto etc – means that it will match up with the default out-the-box parameters as per /etc/racoon/racoon.conf thereby minimizing the amount of tweaking needed on the RedHat machine
All that is needed now is to start the VPN using /etc/sysconfig/network-scripts/ifup ifcfg-ipsec1 and you should be able to communicate between your nodes.


