by R.I. Pienaar | Mar 17, 2009 | Code
I’ve been playing a bit with Stomp and ActiveMQ to help with some of my distributed management problems so needed a nice generic client for it.
I wrote one in Ruby, the code can be found here, you’ll need the Stomp rubygem to use it.
To use it set environment variables STOMP_USER and STOMP_PASSWORD and run it as below, you can also pass the user/pass to it as command line options but that will expose your password in ps output.
% stompclient --server your.server
AMQ> subscribe /topic/foo
Subscribing to /topic/foo
AMQ> /topic/foo bar
Sending 'bar' to /topic/foo
13:48:49:/topic/foo> bar
AMQ> detail
No longer showing details
AMQ> /topic/foo bar
Sending 'bar' to /topic/foo
bar |
% stompclient --server your.server
AMQ> subscribe /topic/foo
Subscribing to /topic/foo
AMQ> /topic/foo bar
Sending 'bar' to /topic/foo
13:48:49:/topic/foo> bar
AMQ> detail
No longer showing details
AMQ> /topic/foo bar
Sending 'bar' to /topic/foo
bar
So it’s just a simple little frontend, it uses Ruby’s readline library which slows things down a bit as it does some blocking polling of input, if you’re sending loads of messages directed at this client it will seem a bit sluggish, unavoidable unfortunately.
by R.I. Pienaar | Mar 11, 2009 | Usefull Things
In the 7 or 8 years I’ve been living in the UK I’ve never been near a fast ADSL exchange, this has all now changed since moving last week and now I can get a BE link, it really is amazing to go from a shoddy 2 Mbit link to 17ish one, see below.
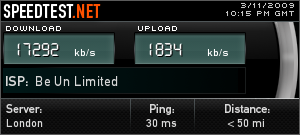
I only activated it this morning, so yet to see if it will be more stable than my previous link which used to drop 3 to 5 times daily, but hopefully now I’ll be abe to play Xbox games while my partner browse stuff, something which previously was totally out of the question.
by R.I. Pienaar | Jan 26, 2009 | Front Page, Usefull Things
I’ve previously mentioned the really great syscfg integrated IPSEC on RedHat Linux here but thought I’d now show a real world example of a Cisco ASA and a RedHat machine talking since it is not totally obvious and it is not something I seen specifically documented anywhere using Google.
A quick recap: RedHat now lets you build IPSEC VPNs using just simple ifcfg-eth0 style config files.
I’ll quickly show both sides of the config to build a site to site VPN, Site A is a Linux machine with a real IP address while Site B is a Cisco ASA with a private network behind it, the Linux machine has this in /etc/sysconfig/network-scripts/ifcfg-ipsec1:
TYPE=IPSEC
ONBOOT=yes
IKE_METHOD=PSK
SRCGW=1.2.3.4
DSTGW=2.3.4.5
SRCNET=1.2.3.4/32
DSTNET=10.1.1.0/24
DST=2.3.4.5
AH_PROTO=none |
TYPE=IPSEC
ONBOOT=yes
IKE_METHOD=PSK
SRCGW=1.2.3.4
DSTGW=2.3.4.5
SRCNET=1.2.3.4/32
DSTNET=10.1.1.0/24
DST=2.3.4.5
AH_PROTO=none
The pre-shared key is in /etc/sysconfig/network-scripts/keys-ipsec1 as per the RedHat documentation.
The Cisco ASA does not support AH so the big deal here is to disable AH which turns out to be the magic knob to tweak here to make it work.
In this case the Linux Server on Site A has the IP address 1.2.3.4 while the ASA is running on 2.3.4.5, the private network at Site B is 10.1.1.0/24.
On the Cisco the relevant lines of config are:
object-group network siteb_to_sitea_local_hosts
description Site B to Site A VPN Local hosts
network-object 10.1.1.0 255.255.255.0
object-group network siteb_to_sitea_remote_hosts
description Site B to Site A VPN Remote Hosts
network-object 1.2.3.4 255.255.255.255
access-list siteb_to_sitea_vpn extended permit ip object-group siteb_to_sitea_local_hosts object-group siteb_to_sitea_remote_hosts
access-list inside_nat_bypass extended permit ip object-group siteb_to_sitea_local_hosts object-group siteb_to_sitea_remote_hosts
nat (inside) 0 access-list inside_nat_bypass
crypto map outside_map 20 match address siteb_to_sitea_vpn
crypto map outside_map 20 set pfs
crypto map outside_map 20 set peer 1.2.3.4
crypto map outside_map 20 set transform-set ESP-3DES-SHA
crypto map outside_map 20 set security-association lifetime seconds 3600
crypto map outside_map 20 set security-association lifetime kilobytes 4608000
crypto map outside_map interface outside
crypto isakmp enable outside
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto isakmp policy 20
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 28800
tunnel-group 1.2.3.4 type ipsec-l2l
tunnel-group 1.2.3.4 ipsec-attributes
pre-shared-key secret |
object-group network siteb_to_sitea_local_hosts
description Site B to Site A VPN Local hosts
network-object 10.1.1.0 255.255.255.0
object-group network siteb_to_sitea_remote_hosts
description Site B to Site A VPN Remote Hosts
network-object 1.2.3.4 255.255.255.255
access-list siteb_to_sitea_vpn extended permit ip object-group siteb_to_sitea_local_hosts object-group siteb_to_sitea_remote_hosts
access-list inside_nat_bypass extended permit ip object-group siteb_to_sitea_local_hosts object-group siteb_to_sitea_remote_hosts
nat (inside) 0 access-list inside_nat_bypass
crypto map outside_map 20 match address siteb_to_sitea_vpn
crypto map outside_map 20 set pfs
crypto map outside_map 20 set peer 1.2.3.4
crypto map outside_map 20 set transform-set ESP-3DES-SHA
crypto map outside_map 20 set security-association lifetime seconds 3600
crypto map outside_map 20 set security-association lifetime kilobytes 4608000
crypto map outside_map interface outside
crypto isakmp enable outside
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto isakmp policy 20
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 28800
tunnel-group 1.2.3.4 type ipsec-l2l
tunnel-group 1.2.3.4 ipsec-attributes
pre-shared-key secret
Using these specific phase 1 and phase 2 parameters – timings, pfs, crypto etc – means that it will match up with the default out-the-box parameters as per /etc/racoon/racoon.conf thereby minimizing the amount of tweaking needed on the RedHat machine
All that is needed now is to start the VPN using /etc/sysconfig/network-scripts/ifup ifcfg-ipsec1 and you should be able to communicate between your nodes.
by R.I. Pienaar | Jan 19, 2009 | Uncategorized
I’ve not posted here for a while, been insanely busy but today those lovely people at Cogent kicked me out of my blogging slumber with a shocking display that I simply had to share.
Cogent for those who do not know is a very large Tier 1 ISP, known mostly for many disputes with other ISPs about peering, it has become so bad that in the UK at least they are basically a complete no-go zone for anyone.
I’ve previously delt with Cogent when a client signed up for a few mbit of Cogent bandwidth on the basis of a £5/mbit pricing structure, they soon realised that you get what you pay for. Even between racks in the same Data Center you could not reach each other without first hopping over to Europe. I’ve attempted to resolve this at the time with Cogent and the other ISPs and both confirmed that it is essentially a waste of time. Cogent said they can’t speak to the ISP in question since most of the UK ISP industry can’t stand them. The other ISP basically laughed out loud about being ‘suckered’ into buying Cogent bandwidth.
This is confirmed elsewhere, search the Renesys Blog for Cogent and you’ll find a lot of information about Cogent, mostly bad news. From an article on their blog about Cogent in the UK you will see this:
Firstly, Cogent has a fairly serious Europe problem right now. They
have been aggressively attacking the European market for a few years
now and making some solid headway. They bought a couple of carriers
(Lambdanet Spain and France, Carrier1 in Germany among them), ruthlessly
integrated them and then proceeded to undersell the market by a factor
of 50-80%. This has made them many enemies.
As a result of this approach to business, Cogent has much less
effective peering in Europe than do many of its larger competitors.
Most of the European PTTs refuse to peer with Cogent anywhere on the
European continent. Recently, some large US carriers (among them
Level (3) ) seem to have adopted a similar approach. This means that
when Cogent sells capacity in Europe, it is forced to drag that
traffic back to the US to hand it off to its peers here. Of course
that means that if the ultimate destination is European, the traffic
has to travel back. This is a burden on both Cogent and the European
carrier and, of course, the customers on both sides. But it’s
unlikely to change because of just how much hate there is for Cogent
among European networkers.
This basically confirms my experience with Cogent and those of many I have spoken too. As such if you choose to support Cogent you will basically be forced to:
- Buy a lot of other bandwidth since if you’re hoping to serve UK customers, Cogent is a terrible sole carrier to have
- You will need to invest in extra hardware, extra admin time, extra complex routing infrastructure and additional overhead on your teams
- You will forever be at the mercy of everyone who hates Cogent, you will find your self randomly falling off the internet, randomly de-peering with vast swaths of the internet and basically the whole thing will be a pain in the behind.
For these reasons, everyone who I know with Cogent bandwidth use them as last resort backup carriers, they are cheap and basically shit, but ok enough to use as a backup when everything else failed.
Over the last few years Cogent has contacted me direct via email to attempt to sell their wares, always the threads end withe me saying something along these lines:
Furthermore we’d prefer to use companies who do not directly
contact us with marketing material, please remove us from your lists
for future contact.
Today again one of my clients got a mention on Techcrunch which resulted in more spam from Cogent, again to an email address totally unrelated to my business activities, not listed in whois records for the client or anything like that. The sales person even had the nerve to copy the email that the above quote is from in his mail to me asking if I can have a conference with him.
My response was the usual, no we don’t deal with spammers, you were told to leave us alone now please stop bothering us. Which resulted in an amazingly pushy email from the sales person, quoted below:
No doubt that writing when being asked not to is, well, borderline. That
said, it is both of our responsibilities to make sure that all options
are explored. You need to confirm that you are aware of all vendors
information, and mine includes getting it out there.
.
.
Admittedly, this is difficult to resolve via email. However, if I didn’t
think that we could compliment your service, I wouldn’t persist.
This is just amazing, this person really think he can presume to tell me what my responsibilities are, what I need to do, and that I have to indulge his blatant b/s.
After I again pointed out that they were asked to stop mailing me and I pointed out that they were using a private email address held by a UK citizen and as such under the data protection laws they need to stop contacting me when asked, they once again mailed me demanding further information about my customers. They really are on par with simple Viagra spammers.
Does anyone really think this kind of heavy handed tactic gets them business?
The worst part of it is the ISP who currently provide a large part of our b/w are Cogent customers, Cogent Sales people do not think twice to approach clients of their clients and try to undercut them – effectively trying to steal their customers business away from them.
Why would any business support such a company? I would not, I would effectively be negligent in my duties to my clients to ever recommend these clowns for anything since they are just a nightmare waiting to happen.
by R.I. Pienaar | Oct 11, 2008 | Usefull Things
I live in a pretty typical for London double story house, my study is upstairs with TV etc downstairs. Till now I just use a Wireless N router to get connectivity downstairs but it’s proven to be less than reliable. Additionally my ADSL router was upstairs – but on an extension and not on the main plug, it’s a recipe for disaster.
I’ve considered many options, long cables and all sorts of things like this. Today while wandering through PC shops trying to find a decent USB reader I again noticed the Homeplug devices and thought I’ll give them a try.
I bought 3 units of the Devolo dLAN 200 AVeasy units, they are 200Mbps maximum devices and support all sorts of fancy things like AES Encryption and basically an ACL of sorts to only allow certain devices to talk to each other. You can essentially create a VLAN by giving groups of devices different passwords etc.
At first I was fairly sceptical but figured it’s worth a shot, I am glad to say the devices totally exceeded my wildest expectations.
Installation was a breeze, pop them into the wall, plug in cables and it all just work. Of course it is not secured by default so I went digging through their site, the docs and so forth is pretty crap to say the least but I found software for Linux, Windows and OS X to manage them. Each device has a security id on the back and you just type the keys for all your devices into the app and provide a password. This gets used to secure the network with AES.
I have now moved my router and firewall machine downstairs to the main socket – ADSL is now much stabler – and have moved the Wifi router downstairs too via the Devolo units. Overall the whole setup just works great, even my Xbox is working great again after my old Wireless Bridge died.
I use a 1GB switch on my LAN and get around 0.3ms ping times in general, if I ping a device on the other end of the Devolo units ping times are around 4ms, transfer speeds over the units are around 7MB/sec when using scp, these figures are very respectable and much better than I had hoped for in the past while considering them.
At +- 50 GBP per unit and the sacrifice of a wall socket its a pretty expensive solution (other manufacturers apparently have ones that act as a network and power adapter so you don’t waste a port) but for me this has proven to be an excellent solution and completely sorted out my network reliability issues.


