by R.I. Pienaar | Nov 4, 2005 | Usefull Things
A day or so ago RELENG_6_0_0_RELEASE got tagged, I also noticed that if you retrieve RELENG_6 you’ll get FreeBSD 6.0 STABLE. I upgraded a few machines to STABLE and have been quite happy so far. Right now the ISO images for 6.0-RELEASE is on the Main FreeBSD FTP Server ready for the taking.
As have been announced all over FreeBSD has decided to move the friendly daemon logo to the side to get something a bit more corporate. A few days ago they announced the new logo and said they’d update the site soon.
So far the first real knock on of this change in Logo and direction is obvious the moment the install CD boots, you’re greeted with this:
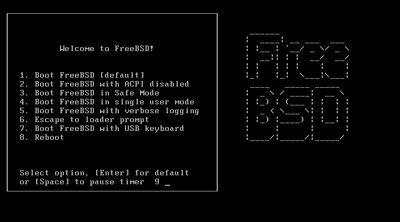
Any long term BSD users will immediately spot the absence of the old ASCII Art BSD Daemon. I like the new logo, but it’s a sad day either way.
by R.I. Pienaar | Nov 3, 2005 | Uncategorized
Anyone who has been reading my blog for a while know that I’ve got no time for Feedster and don’t mind saying so. My previous posts on this sad sad service:
So why do I rehash all this again now? Because if you look at those entries you’ll always see someone from Feedster post about how they’re improving, how I shouldn’t give up on them etc, but really it’s all just talk.
Tonight while trying to figure out why BSDUpdates is down I tried a Google blogs search but found little recent info, so I figured I’ll give Feedster another try, big mistake.
It also had very little useful content so I’m inclined to think people just don’t blog about BSDUpdates – fair enough. The problem is though Feedster is still broken!
First I do a search for ‘bsdupdates’ using the main feedster page, that went well and I found some stuff, then I tried the blog search button which will restrict the search to just blog posts. First there is the fact that the user experience is crap, if you do a Google search for whatever and click on one of the other search modes – like Images – it will know you searched for whatever and show you results immediately. Not feedster, no way, you have to just type your query in again.
So I type it in again, and get a page full of result, it looks like the screenshot below, all good so far.
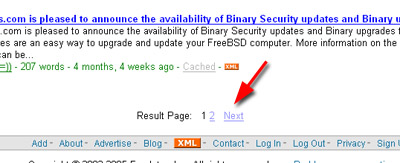
See, next page, more results, all good there is hope for finding something useful, so I press on the next button.
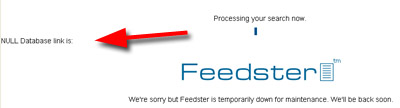
Wtf? Maintenance? Seems more like their default internal server error page is claiming every problem is Maintenance related because this is not the first time I’ve seen it, and I don’t use this service often. It’s a bit like when the Underground in London says something is ‘Signal Failure’ it’s just something they say. The real problem seems to be database related.
So back a page, reload, do the search again which gives me (immediately, right in the middle of their ‘maintenance’ no less) a page similar to the first one. Try the next button again to get the promised more results:
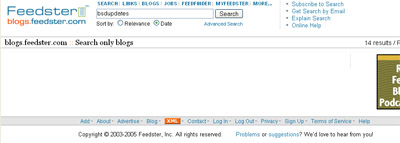
And there it is, nothing, empty page, no results. Complete. Waste. Of. Time.
If you are still using Feedster you really should be doing yourself a favor and jump ship. There are a number of competitors, I can’t even list them all but here are some: Clusty, Blogdigger, Blogpulse, Daypop, Technorati, Google Blog Search, Yahoo! and many more. Natural selection on the internet is a great thing, Feedster had a chance to do it right but they didn’t. The big boys will run over them, rejoice.
by R.I. Pienaar | Nov 3, 2005 | Code
Portaudit is intended to run daily against your ports directory identifying known vulnerabilities against a central database. Each night it produce an email that gets sent out and requires inspection.
The problem with this is with many FreeBSD hosts the emails can just be too many and I tend not to look at them.
Portaudit Central provides a means for delivering portaudit output to a central email box which will then produce a simple HTML based report of all machines. You can view a Sample Report produced using these scripts.
The server side script will call logger(1) with some useful diagnostic messages but the lines being logged will include some variables from the environment. I developed this under exim and the environment variables it logs are set by Exim. This will still work under another MTA, the worst that will happen is you’d have some logging entries thats missing details like the sender and message id.
I’ve taken some steps to prevent man-in-the-middle attacks. An attacker can in theory produce a report that says you have no vulnerabilities on a host when in fact you do have some. In order to combat this a few things are done:
- Only 1 report per host per day, any reports after the first one will result in errors being logged, this should be a clear indication that you’ve either configured multiple clients with the same $hostname or someone is up to no good.
- Each email being sent has a very simple crypto signature, the signature is basically a MD5 hash of the body of the message and a passphrase md5(body, passphrase) this means as long as your passphrases are secure – they aren’t being sent along in the email so no-one can sniff them – someone else should not be able to produce a report that will pass this check regardless of report content. Even if your passphrase gets compromised you should be alerted about tampering by the log entries produced by the duplicate checking mechanism above. As long as you monitor your log files.
I’ve used this system myself now for around a month and have been quite happy, but no-one else has had a look at it yet so I’d appreciate feedback if anyone use it. In the future I hope to make the output from the report generator themed, right now it’s very ugly but it does what it should. I will also move to a actual configuration file rather than editing some perl variables. I’m open to other suggestions.
Version 1.0 can be downloaded here: portauditcentral-current.tgz the full documentation including installation instructions can be found at the Wiki
by R.I. Pienaar | Nov 2, 2005 | Usefull Things
I’ve previously posted about Truecrypt and mentioned how much I like it and how I’m using for my OTFE needs.
Today they released version 4 which comes with a very long list of enhancements the most significant new feature is support for Linux and binaries for a number of distributions. There are so many enhancements in this version that I won’t attempt to go into much detail here the history file does a great job. If you use Truecrypt then check out the new version today.
by R.I. Pienaar | Nov 1, 2005 | Code
I run a number of jail on my servers and each of these have the same files over and over, the biggest problems are of course /usr/ports and /usr/src, they’re a total waste of space and a lot of work running multiple portsnap’s etc to keep them all synced.
BJE mentioned he is using nullfs to mount his main /usr/ports into the jails. I did some hunting of information on this and found its a bit thin on the ground, the main reason is that up till 6.0 it’s considered broken, though testing shows it works ok, at least for normal use.
FreeBSD 6.0 will have extensions to its rc.conf to make all of this easy.
You can create per-jail fstab files, by default they are stored in /etc/fstab.jailname but you can override the filename using jail_example_fstab. Below is a sample fstab file for one of my jails:
/usr/ports /jails/example/usr/ports nullfs rw 1 1
/usr/src /jails/example/usr/src nullfs ro 1 1
To enable the mounting of these file systems at boot time if you use the rc.conf method of booting your jails simply add a jail_example_mount_enable=”YES” to your jail section. A full rc.conf extract to start one example jail below:
jail_enable=”YES”
jail_list=”example”
jail_socket_unixiproute_only=”YES”
jail_sysvipc_allow=”NO”
jail_example_rootdir=”/jails/example”
jail_example_hostname=”example.com”
jail_example_ip=”192.168.1.100″
jail_example_exec=”/bin/sh /etc/rc”
jail_example_devfs_enable=”YES”
jail_example_fdescfs_enable=”NO”
jail_example_procfs_enable=”YES”
jail_example_devfs_ruleset=”devfsrules_jail”
jail_example_mount_enable=”YES”
I’ll investigate also sharing /bin, /sbin, /lib, /libexec, /usr/sbin, /usr/sbin and a few others between jails but it gets a bit tricky if you want to install other versions of perl from ports since they maintain symlinks in /usr/bin etc. This could however simplify world upgrades a lot.
While researching this I came across ezjail which is a script compatible with FreeBSD 6.0 and later to maintain jails that uses nullfs extensively to share a lot of directories from a base jail install. This gives a big potential security improvement because you can mount the system directories read only to give further protection in the event of a compromise. Will definitely investigate this before I start building my new hosted server once FreeBSD 6.0 is out.





